Kubernetes RBAC Best Practices
- maheshchinnasamy10
- Jun 11, 2025
- 2 min read
Introduction:
Role-Based Access Control (RBAC) is a critical security feature in Kubernetes that helps enforce the principle of least privilege. With Kubernetes being widely adopted for container orchestration, it's crucial to manage who can do what inside your clusters.
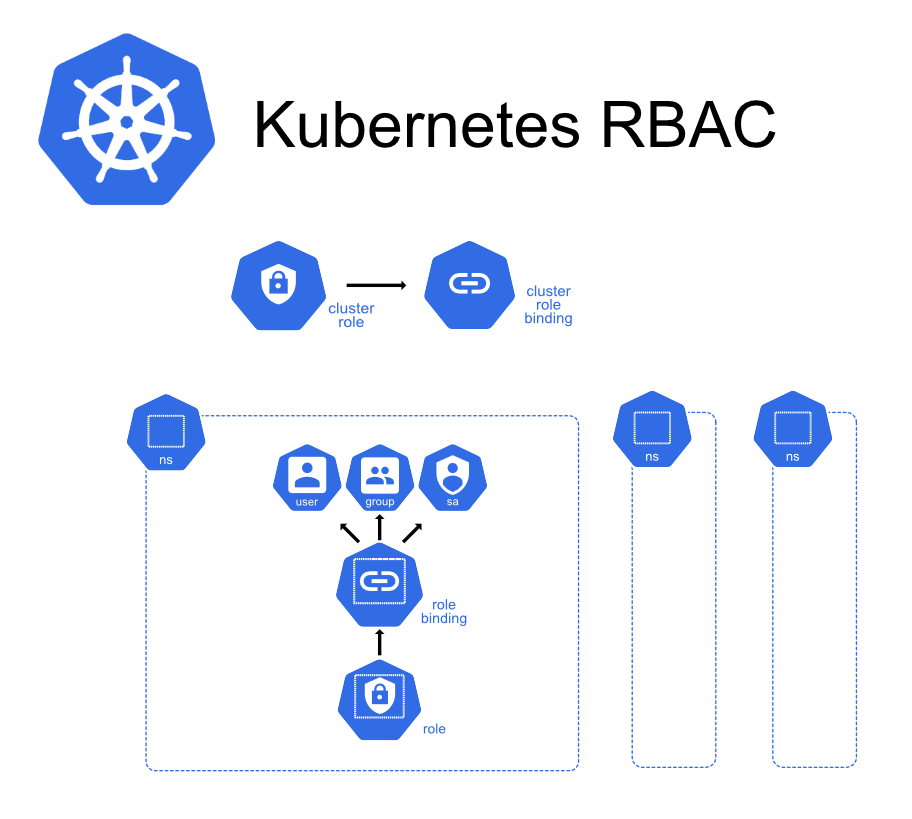
What is Kubernetes RBAC?
RBAC in Kubernetes allows you to define policies that regulate user and application access to cluster resources. It uses four core components:
Role: Defines permissions within a namespace.
ClusterRole: Defines permissions across the entire cluster.
RoleBinding: Grants a Role to a user or group within a namespace.
ClusterRoleBinding: Grants a ClusterRole to a user or group across all namespaces.
Kubernetes RBAC Best Practices:
1. Follow the Principle of Least Privilege
Grant only the permissions that are absolutely necessary for a user or service account.
Use Roles and RoleBindings for Namespace-Level Access
Avoid using ClusterRoles when the access is limited to a single namespace. This improves scope control.
3. Use ClusterRoles Sparingly and Intentionally
Use ClusterRoles only when access to cluster-wide resources (e.g., nodes, persistent volumes) is required.
Examples:
Monitoring tools (access to all pods across namespaces)
Cluster admin users
4. Group Users Using RBAC Bindings
Assign RBAC roles to groups instead of individual users wherever possible. This makes permission management scalable and easier to audit.
5. Regularly Audit and Review Permissions
Over time, access may become overly permissive. Periodically audit role bindings
Use tools like:
Kubeaudit
rakkess (RBAC Access)
6.Use Impersonation for Safer Testing
Before applying permissions, test access with impersonation.
7.Use Read-Only Roles for Observability
Create specific read-only roles for users like QA, SREs, and auditors who only need to view logs or metrics, not modify resources.
8.Document RBAC Policies Clearly
Maintain documentation for:
Who has what access and why
What each Role/ClusterRole is meant for
How to request or revoke access
9.Avoid Default Service Accounts
By default, Kubernetes assigns a service account to pods. Avoid relying on it—define and bind dedicated service accounts with precise access.
10.Use Admission Controllers & Gatekeepers
Enforce RBAC-related policies using OPA Gatekeeper or Kyverno. Example: Prevent creating ClusterRoleBindings unless explicitly allowed.
Conclusion:
RBAC is your first line of defense in Kubernetes security. A well-thought-out RBAC strategy ensures that only the right entities have access to the right resources at the right time. Following these best practices helps avoid security risks, reduces human error, and keeps your Kubernetes environment compliant and secure.



Comments